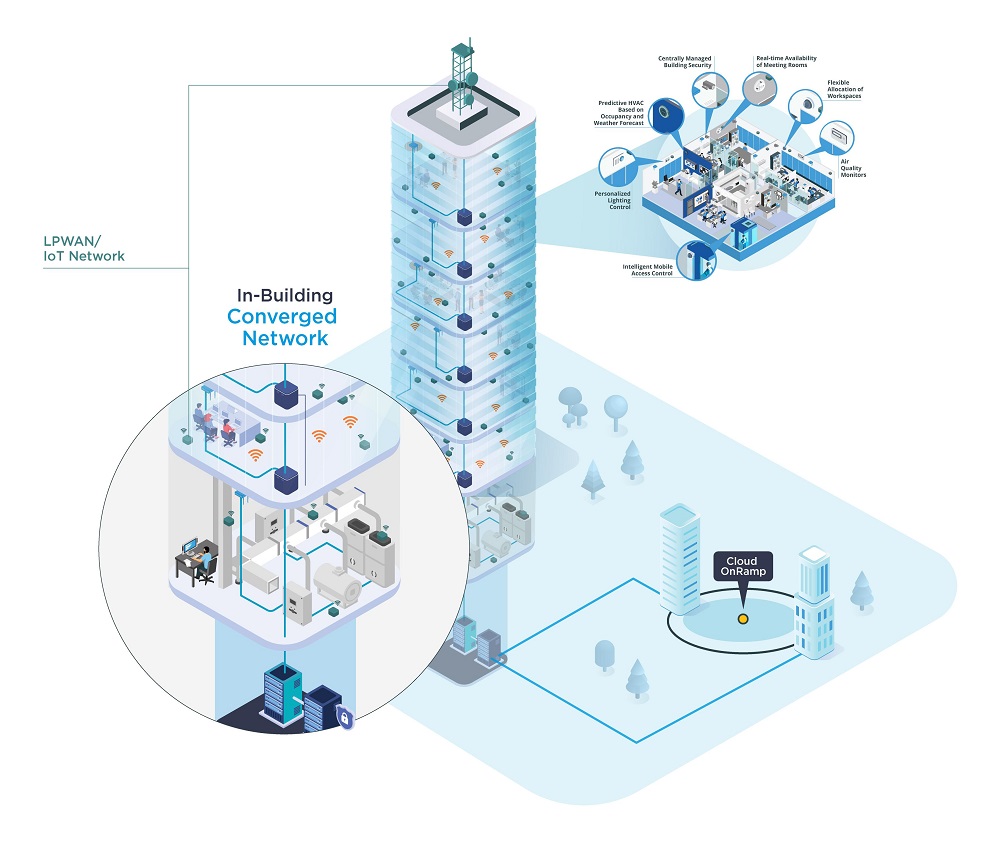
In today's hyper-connected world, the ability to access IoT devices beyond the boundaries of your local network is no longer a luxury but a necessity for both businesses and individuals. Whether you're managing smart home appliances or monitoring industrial equipment remotely, understanding how to establish secure connections to IoT devices outside your network is vital. This guide provides a detailed roadmap to achieving this while ensuring top-tier security.
As more devices join the Internet of Things (IoT), the demand for remote access continues to escalate. From smart thermostats to advanced industrial sensors, the ability to control and monitor these devices from anywhere in the world can dramatically enhance productivity and convenience. However, with this power comes a significant responsibility, particularly in the realm of cybersecurity.
This article is designed to offer you a thorough understanding of how to access IoT devices from outside your network. We’ll delve into everything from establishing secure connections to resolving common issues. By the conclusion of this guide, you'll be equipped with the knowledge and tools needed to ensure your IoT devices remain both accessible and secure.
- Ruth Chris Private Event
- Maine Cabin Masters Jedi
- Billings Mt
- Quality Inn Hotel Ocean City Md
- What Happened To Kevin Gates
Table of Contents
- Understanding IoT
- The Importance of Remote IoT Access
- Approaches to Access IoT from Outside Your Network
- Ensuring Secure Remote IoT Access
- Addressing Common Challenges
- Best Practices for Managing Remote IoT Access
- Essential Tools and Software for IoT Remote Access
- Real-World Case Studies
- The Evolving Landscape of IoT Access
- Final Thoughts
Understanding IoT
The Internet of Things (IoT) is a network of physical objects embedded with sensors, software, and connectivity capabilities, enabling them to exchange data seamlessly. These devices span a wide spectrum, from basic household gadgets to sophisticated industrial machinery. IoT technology has transformed the way we interact with our surroundings, offering unprecedented levels of automation and efficiency.
How IoT Operates
IoT devices function by gathering data through sensors and transmitting it to a central server or cloud platform for analysis. This data can then be accessed and interpreted by users via mobile applications, web interfaces, or other connected devices. The ability to remotely access IoT data is one of the defining features that make IoT technology so impactful.
Benefits of IoT
- Enhanced operational efficiency
- Superior user experience
- Significant cost savings through automation
- Real-time data monitoring and analytics
The Importance of Remote IoT Access
Accessing IoT devices from outside your local network offers numerous advantages. It empowers users to monitor and control their devices from virtually any location, providing unparalleled flexibility and convenience. For businesses, the ability to remotely access IoT devices can lead to increased productivity, improved decision-making, and streamlined operations.
Primary Reasons for Remote IoT Access
- Efficient remote monitoring and management
- Enhanced security through centralized oversight
- Improved collaboration among teams
- Cost-effective maintenance and troubleshooting
Approaches to Access IoT from Outside Your Network
There are multiple methods to access IoT devices remotely, each with its own set of advantages and limitations depending on the specific use case and security requirements.
1. Port Forwarding
Port forwarding involves configuring your router to direct incoming traffic to a specific device within your local network. While this method is relatively straightforward to set up, it can introduce security risks if not meticulously configured.
2. Virtual Private Network (VPN)
A Virtual Private Network (VPN) establishes a secure tunnel between your device and the IoT network, enabling you to access devices as if you were on the local network. This approach offers enhanced security but may necessitate additional setup and maintenance efforts.
3. Cloud-Based Solutions
Cloud-based platforms provide a centralized hub for managing and accessing IoT devices. These platforms often come equipped with built-in security features and are easily scalable as your IoT infrastructure expands.
Ensuring Secure Remote IoT Access
Security is indispensable when accessing IoT devices from outside your network. Without robust security measures, your devices could be susceptible to cyberattacks, potentially leading to data breaches and other severe consequences.
Key Security Strategies
- Employ strong, unique passwords for all devices
- Enable two-factor authentication (2FA) whenever feasible
- Regularly update firmware and software to patch vulnerabilities
- Encrypt data transmissions using protocols like SSL/TLS
Addressing Common Challenges
While remote IoT access presents numerous benefits, it also introduces several challenges. Understanding these obstacles and how to overcome them is crucial for a successful implementation.
Challenge 1: Connectivity Issues
A common issue is maintaining a reliable connection to remote IoT devices. This can be mitigated by leveraging dependable internet service providers and ensuring devices have sufficient signal strength.
Challenge 2: Security Risks
Cybersecurity threats are a significant concern when accessing IoT devices remotely. Implementing comprehensive security measures, such as firewalls and intrusion detection systems, can help alleviate these risks.
Best Practices for Managing Remote IoT Access
To ensure a secure and efficient remote IoT setup, adhere to these best practices:
1. Conduct Regular Network Audits
Perform routine security audits to identify and address potential vulnerabilities within your IoT network.
2. Monitor Device Activity
Utilize monitoring tools to track device activity and detect any unusual behavior that may indicate a security breach.
3. Educate Users
Provide training and resources to users on how to securely access and manage IoT devices, fostering a culture of security awareness.
Essential Tools and Software for IoT Remote Access
A variety of tools and software solutions are available to facilitate remote IoT access. These tools frequently include features like device management, data analytics, and security monitoring.
Popular IoT Platforms
- Amazon Web Services IoT Core
- Microsoft Azure IoT Hub
- Google Cloud IoT Core
Real-World Case Studies
Real-world examples provide valuable insights into how organizations are successfully implementing remote IoT access. For instance, a manufacturing company might use IoT sensors to monitor equipment performance and schedule maintenance remotely, minimizing downtime and reducing costs.
Example: Smart Agriculture
In the agricultural sector, farmers employ IoT devices to monitor soil moisture levels and weather conditions. By accessing this data remotely, they can make well-informed decisions about irrigation and crop management, resulting in higher yields and improved resource efficiency.
The Evolving Landscape of IoT Access
The future of IoT access is bright, with technological advancements driving innovation in remote connectivity. Emerging trends such as edge computing and 5G networks are expected to enhance the capabilities of IoT devices, making remote access faster and more reliable.
Key Trends to Watch
- Edge computing for accelerated data processing
- 5G networks for superior connectivity
- Artificial intelligence for predictive maintenance
Final Thoughts
Accessing IoT devices from outside your network is a powerful capability that can significantly boost productivity and convenience. By adhering to the best practices outlined in this guide and implementing robust security measures, you can ensure your IoT devices remain both accessible and secure.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT technology and its applications.
References:
- IEEE Internet of Things Journal
- Forrester Research Reports
- Gartner IoT Predictions

Detail Author:
- Name : Marlon Rippin
- Username : ron.lebsack
- Email : kschimmel@hotmail.com
- Birthdate : 1979-05-21
- Address : 91465 Neil Brook Apt. 946 Raynorshire, DE 96506
- Phone : +1-480-582-1919
- Company : Stroman Ltd
- Job : Archivist
- Bio : Earum odit recusandae aut reprehenderit. Odit velit ex velit voluptatem tempore id. Quo quia sequi ipsum. Eius sunt sint eveniet voluptatem aut nemo ea sed.
Socials
linkedin:
- url : https://linkedin.com/in/reicherte
- username : reicherte
- bio : Nostrum qui dolores voluptate ut.
- followers : 2593
- following : 1616
facebook:
- url : https://facebook.com/elinor_reichert
- username : elinor_reichert
- bio : In labore nihil sapiente. Dolores ad qui omnis inventore deleniti repudiandae.
- followers : 5880
- following : 460