IPTables PREROUTING is a robust feature in Linux that empowers administrators to modify network packets at an early stage, before they reach the intended application. This capability is crucial for network security, load balancing, and efficient traffic management. Whether you're a beginner or an experienced network administrator, mastering IPTables PREROUTING can significantly enhance your ability to address complex networking challenges.
In today's rapidly evolving digital landscape, safeguarding your network infrastructure from increasingly sophisticated cyber threats has become more critical than ever. IPTables PREROUTING provides an effective mechanism for filtering, altering, and routing incoming packets, ensuring that only legitimate traffic reaches your system. By gaining proficiency in this feature, you can strengthen your network's security and optimize resource utilization, paving the way for a more resilient and efficient network infrastructure.
This article delves deep into the world of IPTables PREROUTING, offering a detailed exploration of its fundamental concepts, practical applications, and advanced configurations. Regardless of your current expertise level, this guide equips you with the knowledge and tools necessary to harness the full potential of IPTables PREROUTING, enabling you to create secure and high-performing network environments.
- Outlet Centermithfield Nc
- Best Blue Oyster Cultongs
- Amazon Prime Call Center
- Shopritetore Locator Pa
- What Happened To Kevin Gates
Table of Contents:
- Exploring IPTables PREROUTING
- Understanding IPTables
- The Role of the PREROUTING Chain
- Practical Applications of IPTables PREROUTING
- Configuring IPTables PREROUTING
- Advanced Techniques for PREROUTING
- Resolving Common Issues
- Boosting IPTables PREROUTING Performance
- Security Best Practices
- Conclusion and Recommendations
Exploring IPTables PREROUTING
IPTables PREROUTING is a fundamental component of the Netfilter framework, designed to allow packet manipulation before routing decisions are made. This chain is particularly advantageous for modifying packets destined for the local machine or those being routed through the system. By intercepting packets early in the network stack, administrators can establish advanced rules for packet filtering, address translation, and other critical network operations.
In the realm of network security, IPTables PREROUTING serves as a vital protective layer by enabling administrators to enforce stringent access controls and filter out potentially harmful traffic. This capability is especially beneficial in environments exposed to external threats, such as public-facing servers or cloud-based infrastructures. A solid understanding of the PREROUTING chain requires familiarity with the broader IPTables framework and its associated components. This section will provide a foundational overview of IPTables and the role of the PREROUTING chain within the context of network management.
- Johnny Depp Vanessa Paradis
- Tom And Jerry 2020 Cast
- Bluesongs Lyrics
- Charlieheen Ashton Kutcher
- Premier Row
Understanding IPTables
What is IPTables?
IPTables is a versatile user-space utility that empowers system administrators to configure the tables provided by the Linux kernel's netfilter framework. These tables consist of chains, which are sequences of rules dictating how packets should be processed. IPTables operates on the principle of packet filtering, enabling administrators to control network traffic based on specific criteria, such as source and destination IP addresses, protocols, and ports.
Key Components of IPTables
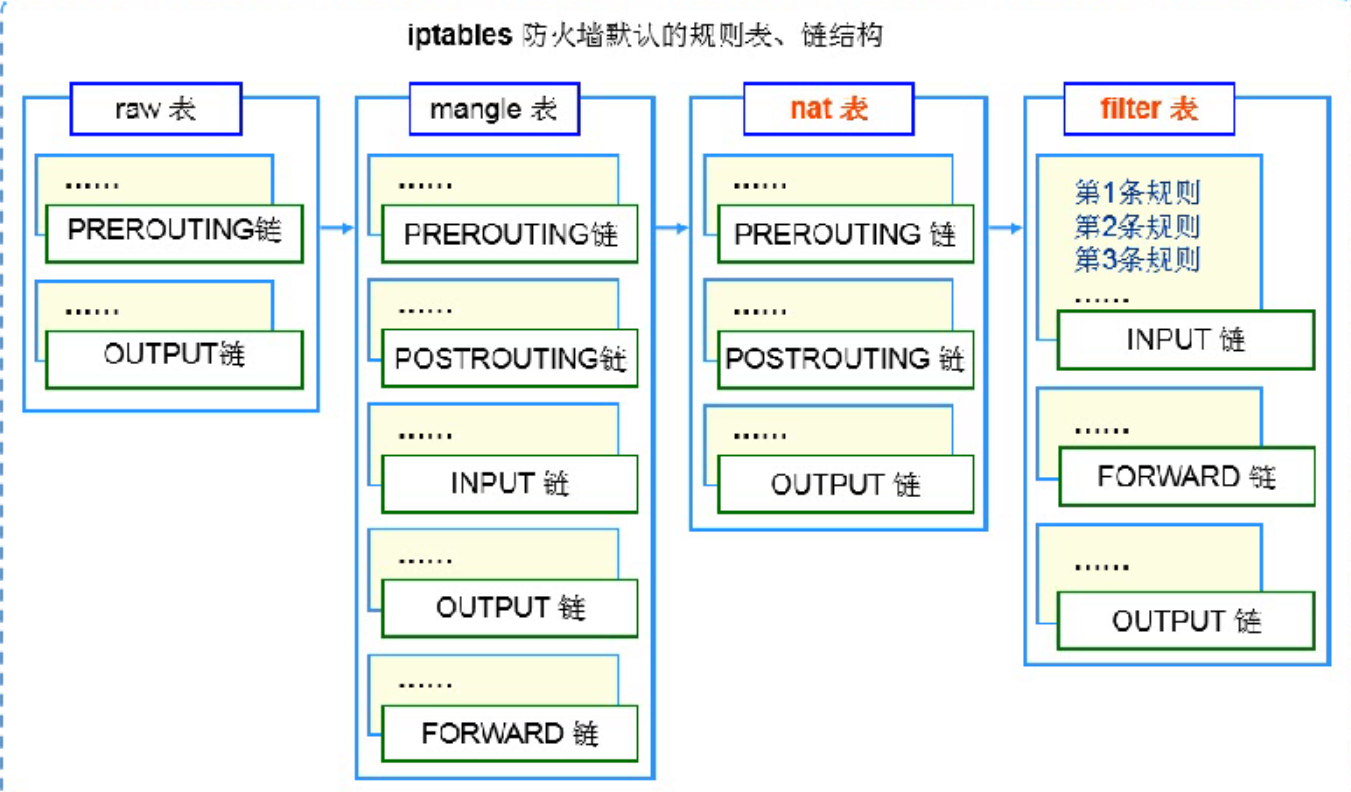
- Tables: IPTables comprises multiple tables, each serving a distinct purpose. The most commonly used tables include filter (for packet filtering), nat (for network address translation), mangle (for specialized packet alterations), and raw (for handling packets before connection tracking).
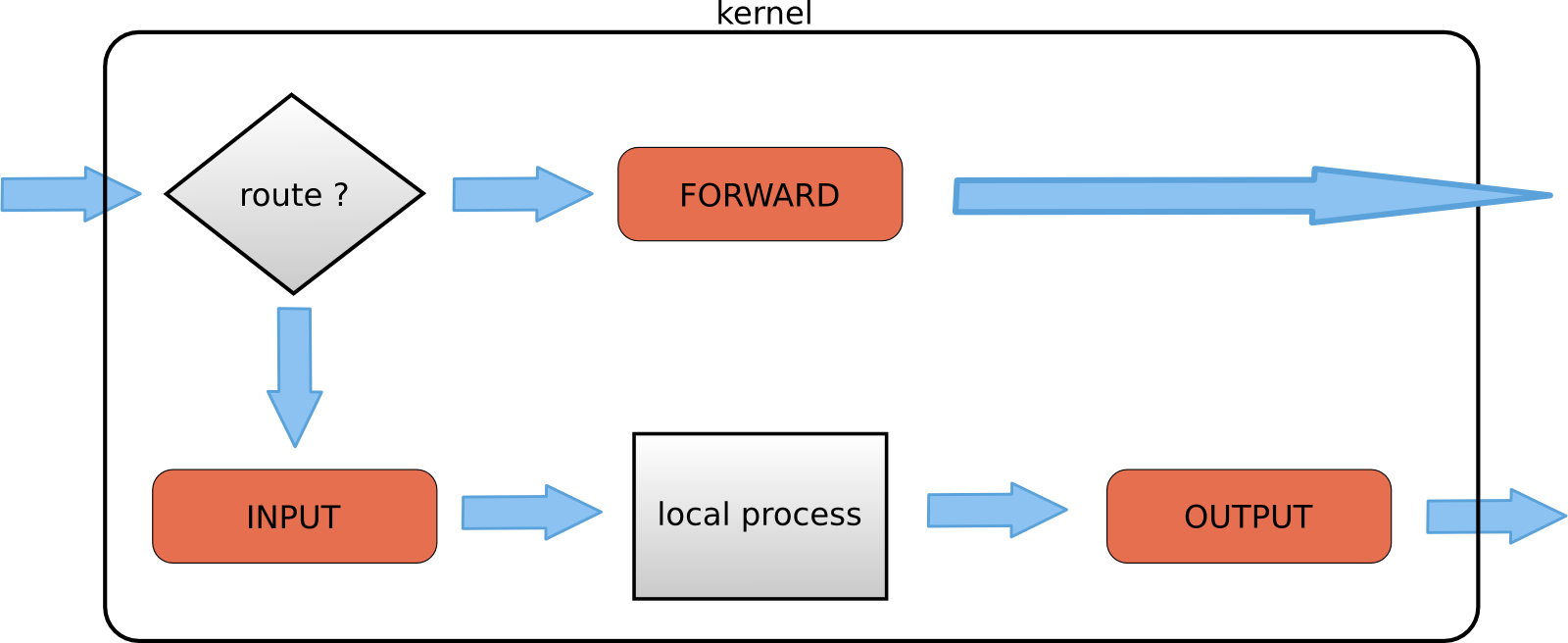
- Chains: Chains are ordered lists of rules within a table. Common chains include INPUT (for incoming packets), OUTPUT (for outgoing packets), FORWARD (for packets passing through the system), PREROUTING (for packets before routing decisions), and POSTROUTING (for packets after routing decisions).
- Rules: Rules define the actions to be performed on packets that match specific criteria. These actions may include accepting, dropping, rejecting, or modifying packets, providing administrators with granular control over network traffic.
Why Use IPTables?
IPTables offers unmatched flexibility and control over network traffic, making it an indispensable tool for administrators seeking to secure their systems. Its seamless integration with the Linux kernel ensures high performance and reliability, making it a preferred choice for both small-scale and enterprise-level deployments. Whether you need to implement basic firewall rules or advanced traffic management strategies, IPTables provides the tools necessary to meet your network's unique requirements.
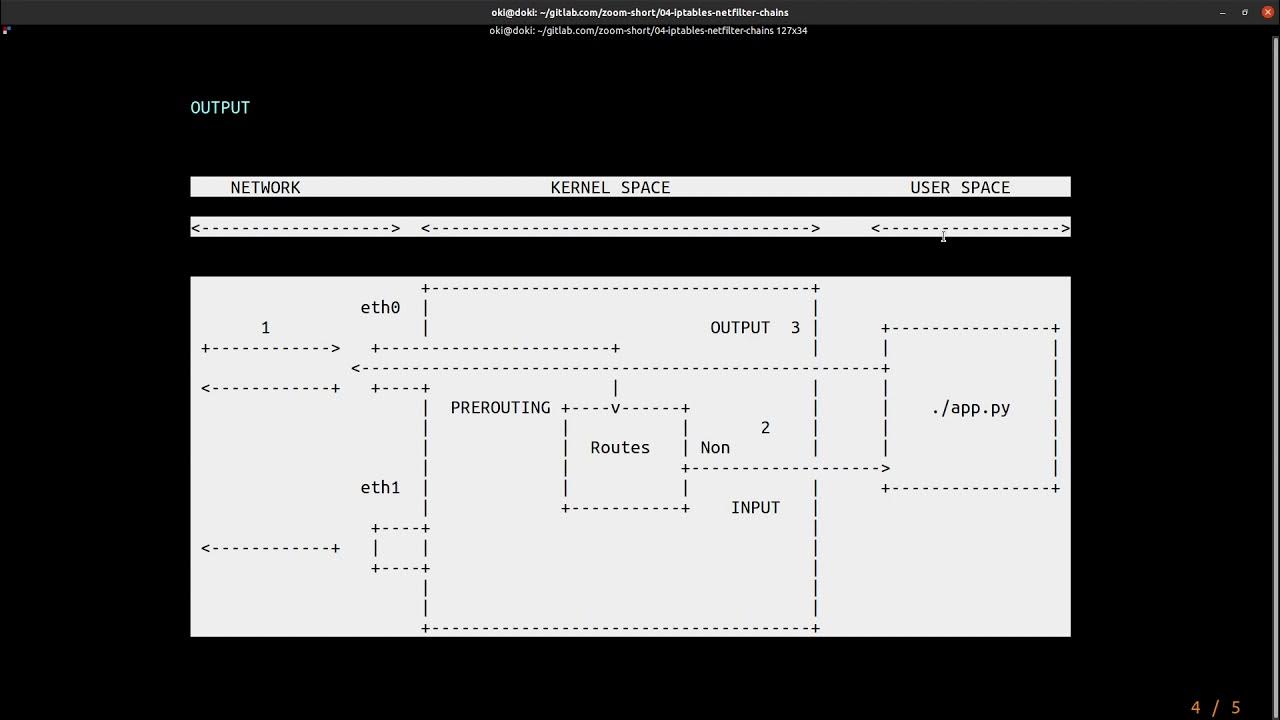
The Role of the PREROUTING Chain
The PREROUTING chain is a vital component of the nat table in IPTables, responsible for processing packets immediately after they enter the system but before any routing decisions are made. This chain is particularly useful for tasks such as Network Address Translation (NAT), port forwarding, and traffic redirection. When a packet arrives, it first passes through the PREROUTING chain, where it can be modified according to predefined rules. These modifications may involve altering the source or destination IP address, changing port numbers, or redirecting traffic to different services.
Understanding the flow of packets through the PREROUTING chain is essential for designing effective firewall rules and optimizing network performance. By leveraging this chain, administrators can implement advanced configurations that not only enhance security but also improve the overall functionality of their network infrastructure.
Practical Applications of IPTables PREROUTING
Port Forwarding
One of the most prevalent use cases for IPTables PREROUTING is port forwarding. This technique allows administrators to redirect incoming traffic from one port to another, enabling services to operate on non-standard ports while maintaining accessibility. For example, you can forward traffic from port 80 to port 8080, allowing a web server to run on the latter while still being accessible via the default HTTP port.
Network Address Translation (NAT)
IPTables PREROUTING plays a critical role in implementing NAT, which involves modifying the source or destination IP addresses of packets. This functionality is invaluable in scenarios where multiple devices share a single public IP address, such as in home or small business networks. By using PREROUTING rules, administrators can ensure that incoming traffic is correctly routed to the appropriate device, enhancing network efficiency and usability.
Traffic Redirection
With IPTables PREROUTING, administrators can redirect traffic to specific services or applications based on predefined criteria. This capability is especially useful for load balancing, content filtering, and enforcing custom network policies. For instance, you can redirect HTTPS traffic destined for a specific IP address to a different server or service, ensuring optimal performance and resource utilization.
Configuring IPTables PREROUTING
Configuring IPTables PREROUTING involves defining rules that specify how packets should be processed. Below are some examples of common configurations:
Basic Port Forwarding
To forward incoming traffic on port 80 to port 8080, you can use the following command:
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 8080
Network Address Translation
For NAT, you can modify the destination IP address of packets using the DNAT target:
iptables -t nat -A PREROUTING -d ORIGINAL_IP -p tcp --dport 22 -j DNAT --to-destination NEW_IP
Traffic Redirection
To redirect traffic destined for a specific IP address to a different service, use the following rule:
iptables -t nat -A PREROUTING -d TARGET_IP -p tcp --dport 443 -j DNAT --to-destination SERVICE_IP:443
Advanced Techniques for PREROUTING
While basic configurations provide foundational functionality, advanced techniques can unlock the full potential of IPTables PREROUTING. Below are some examples:
Load Balancing
By implementing PREROUTING rules with load balancing algorithms, administrators can distribute incoming traffic across multiple servers, ensuring optimal performance and reliability. This approach is particularly beneficial in high-traffic environments where maintaining consistent service levels is crucial.
Content Filtering
Using PREROUTING, administrators can filter incoming traffic based on specific criteria, such as IP addresses, protocols, or content types. This capability is invaluable for implementing security policies and blocking malicious traffic, thereby enhancing the overall security of the network.
Custom Network Policies
With IPTables PREROUTING, administrators can define custom network policies tailored to meet specific organizational requirements. These policies may include traffic shaping, quality of service (QoS) configurations, and other advanced network management techniques, enabling administrators to optimize network performance and resource utilization.
Resolving Common Issues
When working with IPTables PREROUTING, administrators may encounter various challenges. Below are some common problems and their solutions:
Rules Not Applying
If PREROUTING rules are not being applied, ensure that the correct table and chain are being used. Additionally, verify that the rules are in the correct order and that no conflicting rules exist. Properly structuring your rules can prevent unexpected behavior and ensure that your configurations function as intended.
Performance Degradation
Complex PREROUTING configurations can lead to performance degradation, particularly in high-traffic environments. To mitigate this, optimize your rules by removing unnecessary entries and using efficient matching criteria. Streamlining your configurations can significantly improve processing speed and reduce resource consumption.
Unexpected Behavior
In cases of unexpected behavior, review your complete IPTables configuration to identify potential conflicts or misconfigurations. Tools like iptables-save can help in diagnosing issues by providing a comprehensive view of your current rules. Regularly auditing your configurations ensures that your network remains secure and efficient.
Boosting IPTables PREROUTING Performance
Optimizing IPTables PREROUTING involves refining your rules, reducing overhead, and ensuring efficient processing. Below are some strategies for achieving optimal performance:
Rule Simplification
Simplify your rules by combining similar entries and eliminating redundant configurations. This approach reduces the processing overhead and improves overall performance, making your network more efficient and responsive.
Rule Ordering
Place frequently used rules at the top of the chain to minimize the number of comparisons required for packet processing. This technique can significantly enhance performance, especially in high-traffic environments, by allowing packets to be processed more quickly and efficiently.
Using Efficient Matching Criteria
Use specific and efficient matching criteria to ensure that rules are applied only to relevant packets. This approach minimizes unnecessary processing and improves system efficiency, allowing your network to handle traffic more effectively and reliably.
Security Best Practices
Implementing IPTables PREROUTING requires adherence to security best practices to ensure the integrity and confidentiality of network traffic. Below are some recommendations:
Regular Audits
Conduct regular audits of your IPTables configurations to identify and address potential vulnerabilities. This practice ensures that your security policies remain up-to-date and effective, protecting your network from emerging threats and unauthorized access.
Least Privilege Principle
Apply the least privilege principle by granting only the necessary permissions for each rule. This approach minimizes the attack surface and reduces the risk of unauthorized access, enhancing the overall security of your network infrastructure.
Monitoring and Logging
Enable monitoring and logging for IPTables PREROUTING to detect and respond to suspicious activities promptly. Analyzing logs can provide valuable insights into network behavior and help identify potential threats, enabling you to take proactive measures to protect your network.
Conclusion and Recommendations
In conclusion, IPTables PREROUTING is a powerful tool that offers administrators unparalleled control over network traffic. By understanding its functionality and implementing effective configurations, you can enhance your network's security and performance, ensuring that it meets the demands of modern network environments. Whether you're implementing basic port forwarding or advanced load balancing techniques, IPTables PREROUTING provides the flexibility and scalability needed to address complex networking challenges.
We encourage readers to explore the concepts discussed in this article and experiment with IPTables PREROUTING in their own environments. For further learning, consider exploring additional resources on IPTables and network security. Share your thoughts and experiences in the comments section below and contribute to the ongoing dialogue around network management and security.
Detail Author:
- Name : Mrs. Alysson Maggio
- Username : frank.rosenbaum
- Email : bergstrom.euna@gmail.com
- Birthdate : 1992-03-20
- Address : 643 Elissa Ford Port Nicholastown, IL 02370
- Phone : 1-414-202-7685
- Company : Moore-Brown
- Job : Forming Machine Operator
- Bio : Quis sed qui consequatur quidem quisquam quam consectetur omnis. Qui accusamus tempora quos quos rem illum eius. Illo atque dolore est. Enim cupiditate molestias itaque impedit delectus fuga.
Socials
tiktok:
- url : https://tiktok.com/@rueckera
- username : rueckera
- bio : Vitae qui et id asperiores adipisci velit soluta possimus.
- followers : 5130
- following : 2003
linkedin:
- url : https://linkedin.com/in/amos_real
- username : amos_real
- bio : Qui aut soluta reiciendis quaerat et dolor.
- followers : 998
- following : 2122
instagram:
- url : https://instagram.com/ruecker2016
- username : ruecker2016
- bio : Ab cum et sed repudiandae consectetur. Consectetur iure nulla pariatur aliquid enim et aut.
- followers : 1263
- following : 1603
facebook:
- url : https://facebook.com/amos_official
- username : amos_official
- bio : Quia consequatur ipsa provident voluptatem libero dolorem explicabo.
- followers : 4576
- following : 216