In today's digital era, the ability to securely access your server or network from any location has become a necessity for professionals and organizations alike. Whether you're a developer, system administrator, or IT specialist, Secure Shell (SSH) offers a reliable and secure method for managing remote systems. As remote work continues to grow in popularity, the concept of "SSH from anywhere" has gained significant importance. This detailed guide will walk you through everything you need to know about SSH, including its setup, security measures, and best practices.
SSH is more than just a tool—it's a protocol designed to ensure secure communication between devices over potentially insecure networks. By leveraging SSH from anywhere, you can confidently manage your servers and systems without the fear of data breaches or unauthorized access. This guide delves into the intricacies of SSH, offering valuable insights into its significance and practical applications.
Whether you're a beginner or an experienced professional, this article aims to deepen your understanding of SSH and its pivotal role in modern IT infrastructure. By the conclusion of this guide, you'll possess a thorough understanding of how to configure SSH for remote access, fortify your connections, and resolve common issues effectively.
- Welsh Park Rockville Md
- South Bend A Breaking News
- Koa Campground Near Dollywood
- Premier Row
- Amc Grand Prairie
Table of Contents
- Understanding SSH: What It Is and Why It Matters
- The Benefits of Using SSH from Anywhere
- Setting Up SSH for Secure Remote Access
- Enhancing SSH Security: Best Practices
- Troubleshooting Common SSH Issues
- Exploring Advanced SSH Features
- Using SSH Across Different Operating Systems
- SSH from Anywhere in the Cloud: Managing Resources Globally
- Frequently Asked Questions About SSH
- Conclusion: Embracing SSH for Enhanced Security and Productivity
Understanding SSH: What It Is and Why It Matters
Secure Shell (SSH) is a cryptographic network protocol developed to provide secure communication over potentially insecure networks. It serves as a cornerstone for remote login and command execution but extends its utility to file transfers and tunneling. SSH ensures the integrity, confidentiality, and authentication of all data transmitted between the client and server through robust encryption mechanisms.
Operating on a client-server model, SSH enables users to establish secure connections, execute commands, transfer files, and perform various tasks seamlessly. Its widespread adoption by IT professionals is a testament to its exceptional security features and versatility. Moreover, the ability to use SSH from anywhere empowers users to access their servers or networks from any location, provided they have an internet connection and the necessary credentials. This flexibility is indispensable in the fast-paced digital landscape where remote work and global collaboration are increasingly prevalent.
The Benefits of Using SSH from Anywhere
Utilizing SSH from anywhere presents a multitude of advantages for both individuals and organizations. Below are some compelling reasons to consider implementing SSH for remote access:
- Enhanced Security: SSH employs robust encryption techniques to safeguard all data transmitted between the client and server, effectively preventing interception and unauthorized access.
- Flexibility: With SSH, you gain the ability to access your servers from any location, making it an ideal solution for remote work and fostering global collaboration.
- Reliability: SSH is renowned for its stability, ensuring dependable connections even under challenging network conditions.
- Cost-Effectiveness: SSH eliminates the need for expensive hardware or software solutions, offering an economical approach to secure remote access.
- Automation: SSH facilitates the automation of repetitive tasks, such as backups and deployments, saving valuable time and enhancing operational efficiency.
By harnessing the power of SSH from anywhere, you can significantly boost your productivity, strengthen security measures, and optimize your operations. However, adhering to best practices is essential to guarantee the security and reliability of your SSH connections.
Setting Up SSH for Secure Remote Access
Installing an SSH Client on Your Device
To effectively use SSH from anywhere, the first step is to install an SSH client on your device. Most Unix-based systems, including Linux and macOS, come equipped with an SSH client by default. Windows users have the option to utilize tools like PuTTY or the built-in SSH client available in Windows 10.
Here’s how you can install an SSH client on various platforms:
- Linux: SSH is typically pre-installed, but if it isn’t, you can install it using your package manager. For instance, on Ubuntu, execute the command
sudo apt install openssh-client. - macOS: SSH is pre-installed, allowing you to start using it right away.
- Windows: You can activate the built-in SSH client by navigating to Settings > Apps > Optional Features and selecting "OpenSSH Client."
Configuring the SSH Server on Your Remote Machine
Once the SSH client is installed on your device, the next step is to configure the SSH server on your remote machine. The server plays a crucial role in managing incoming SSH connections and authenticating users.
To configure an SSH server on a Linux system, follow these steps:
- Install the SSH server package using the command
sudo apt install openssh-server. - Initiate the SSH service by executing the command
sudo service ssh start. - Modify the SSH server settings in the
/etc/ssh/sshd_configfile. You can adjust parameters such as the port number, authentication methods, and access restrictions to suit your requirements. - After making changes, restart the SSH service using the command
sudo service ssh restart.
Proper configuration of the SSH server is vital for ensuring secure and dependable connections. Always adhere to best practices to safeguard your server from unauthorized access.
Enhancing SSH Security: Best Practices
Although SSH provides a secure method for accessing remote systems, it is imperative to follow best practices to further enhance security. Below are some recommendations to secure your SSH connections:
- Use Strong Passwords: Encourage all user accounts to adopt strong, complex passwords that are difficult to guess.
- Disable Password Authentication: Opt for SSH keys over passwords for authentication to mitigate the risk of brute-force attacks.
- Change the Default Port: SSH usually operates on port 22, but switching to a non-standard port can help deter automated attacks.
- Limit User Access: Restrict SSH access to specific users or groups to minimize the likelihood of unauthorized access.
- Enable Two-Factor Authentication: Enhance security by requiring a second form of authentication, such as a one-time password.
Implementing these best practices can greatly improve the security of your SSH connections and protect your systems from potential threats.
Troubleshooting Common SSH Issues
Even with meticulous configuration, SSH users may encounter challenges from time to time. Below are some common problems and their respective solutions:
- Connection Refused: Confirm that the SSH server is operational and that the firewall permits incoming connections on the specified port.
- Permission Denied: Ensure that the user has the appropriate permissions to access the server and that the authentication method is correctly configured.
- Timeout Errors: Examine the network connection and verify that there are no firewall or routing issues disrupting the connection.
- Key Authentication Issues: Ensure that the SSH key is accurately added to the authorized_keys file on the server and that the file permissions are appropriately set.
Troubleshooting SSH issues necessitates a systematic approach and a comprehensive understanding of the protocol and its configuration. Always consult the SSH logs for detailed information regarding connection issues.
Exploring Advanced SSH Features
SSH Tunneling: A Secure Way to Access Remote Services
SSH tunneling, often referred to as port forwarding, enables secure access to services running on a remote server. This feature proves particularly beneficial for accessing databases, web applications, or other services that are not exposed to the public internet.
To establish an SSH tunnel, utilize the following command:
ssh -L local_port:destination_host:destination_port user@ssh_server
For instance, to access a MySQL database running on port 3306 on a remote server, you can use the command:
ssh -L 3306:localhost:3306 user@ssh_server
SSH Keys: Strengthening Authentication
SSH keys offer a more secure and convenient method of authenticating users compared to passwords. They consist of a public key, which is stored on the server, and a private key, which is securely kept on the client.
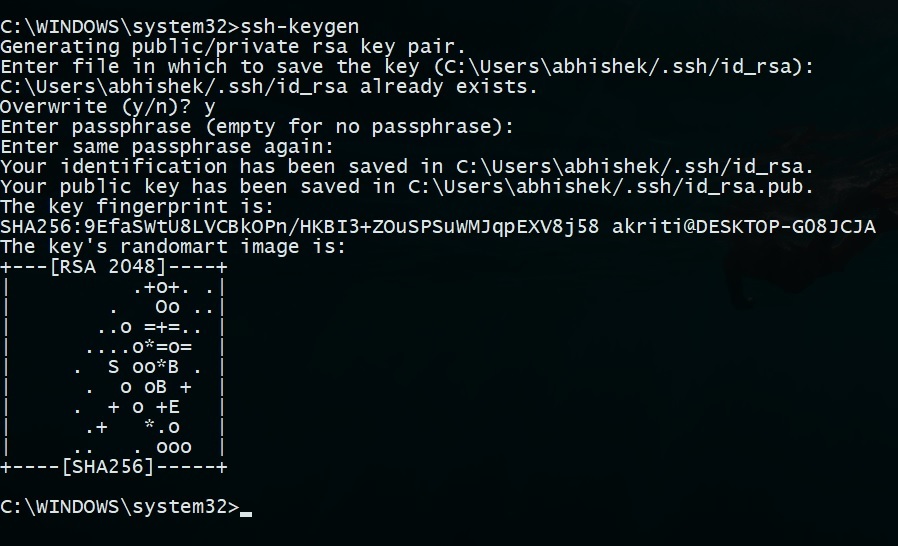
To generate an SSH key pair, use the command:
ssh-keygen -t rsa -b 4096
Once the keys are generated, add the public key to the ~/.ssh/authorized_keys file on the server. You can then authenticate using the private key without the need to enter a password.
Using SSH Across Different Operating Systems
SSH is widely supported across numerous platforms, making it a versatile tool for remote access. Below is a guide on how to use SSH on different operating systems:
- Linux: Use the terminal to connect to a remote server using the command
ssh user@server. - macOS: Open the Terminal app and use the same command as Linux.
- Windows: Utilize the built-in SSH client or tools like PuTTY to connect to remote servers.
Regardless of the platform, the fundamental principles of SSH remain consistent, ensuring a uniform experience across diverse environments.
SSH from Anywhere in the Cloud: Managing Resources Globally
As cloud computing continues to expand, SSH has emerged as a critical tool for managing cloud-based resources. Many cloud providers offer native support for SSH, enabling users to securely access their virtual machines and servers from any location.
To leverage SSH from anywhere in the cloud:
- Create a virtual machine or server within your cloud provider's platform.
- Generate an SSH key pair and upload the public key to the cloud provider's dashboard.
- Connect to the server using the SSH client and your private key.
Cloud-based SSH delivers the same advantages as traditional SSH, with the added convenience of managing resources from anywhere in the world.
Frequently Asked Questions About SSH
Below are some commonly asked questions and answers regarding SSH:
- What is SSH used for? SSH is utilized for secure remote access, file transfers, and tunneling.
- Is SSH secure? Yes, SSH incorporates strong encryption and authentication mechanisms to ensure secure communication.
- Can SSH be used for file transfers? Yes, SSH can facilitate secure file transfers using protocols like SFTP and SCP.
- How do I generate SSH keys? Use the command
ssh-keygen


Detail Author:
- Name : Rebeca Huel
- Username : darrell.koepp
- Email : ulemke@kiehn.org
- Birthdate : 1982-04-20
- Address : 52468 Janae Hills Suite 364 Port Newtontown, WA 91228
- Phone : +1-779-516-3094
- Company : Feest, Waelchi and Rohan
- Job : Rotary Drill Operator
- Bio : Non ut sint quisquam non. Corporis iure laudantium totam sint et. Exercitationem magnam a impedit cupiditate ipsum. In sapiente quisquam unde sed laborum possimus tenetur.
Socials
twitter:
- url : https://twitter.com/nicola8370
- username : nicola8370
- bio : Et tenetur et ducimus voluptatibus ut molestiae omnis. Quasi atque laboriosam ea omnis optio ex. Sit ratione a aperiam sunt.
- followers : 5429
- following : 954
linkedin:
- url : https://linkedin.com/in/nicola_klocko
- username : nicola_klocko
- bio : Doloremque impedit libero dolorem et cupiditate.
- followers : 1737
- following : 396
tiktok:
- url : https://tiktok.com/@klocko2008
- username : klocko2008
- bio : Aut soluta illum sit sequi esse earum. Quam eos ex qui ut.
- followers : 4568
- following : 1393
facebook:
- url : https://facebook.com/nicola7758
- username : nicola7758
- bio : Quia et neque labore. Architecto nesciunt enim et cum incidunt omnis est quae.
- followers : 2807
- following : 567
instagram:
- url : https://instagram.com/nicola.klocko
- username : nicola.klocko
- bio : Sequi omnis qui voluptatem ullam ea rem. Dolor ea iusto quo. Nobis at id quisquam.
- followers : 1207
- following : 2385
